| |
|
|
| |
|
|
|
 |
|
| |
|
Online banking - Important Message
Bank Of America, N.
|
|
|
|
 |
|
 |
| |

|
Date Reported: 21st October 2010  |
Risk Level: MEDIUM  |
|
| |
 |
 |
| |
Email Subject: |
Online banking - Important Message |
|
Apparent Sender: |
Bank Of America, N.  |
|
Return Address: |
A.security@bankofamerica.com  |
|
| Email Format: |
HTML  |
| |
URL of Web Content: |
http://liftmeme.com/upload/boa/boa/sas/cgi-
bin/i
as/A/1/bofa/ibd/IAS/presentation/pm_tokenĀ886KJEHD
89483JSO3829ENDHU8392OJD/safe.ssl.confi
rm.online
bankingofamerica.com/index.html
 |
|
Anchor text of URLs: |
1) Sign
In , 2)
Sign
in to
Online Banking, 3) www.bankofamerica.com  |
|
Location: |
Location not available  |
| |
Scam number: |
13513-186614-457275 |
| |
Comments: |
- Email asks you to confirm/update/verify your account data at Bank Of America, N. by visiting the given link. You will be taken to a spoof website where your details will be captured for the phishers.
- Bank Of America, N. never send their users emails requesting personal details in this way.
- The anchor text appears as a legitimate URL, but don't be fooled - clicking on it will take you to a phishing site!
- The spoof website this email links to was not online at time of this report, but variations of the scam which link to working websites are bound to exist, so be wary! The website may have been taken down or disabled by the hosts, but quite often these websites are hosted on the personal computer of the phishers, so may only be online at certain times.
|
| |
|
|
 |
 |
| |
|
| |
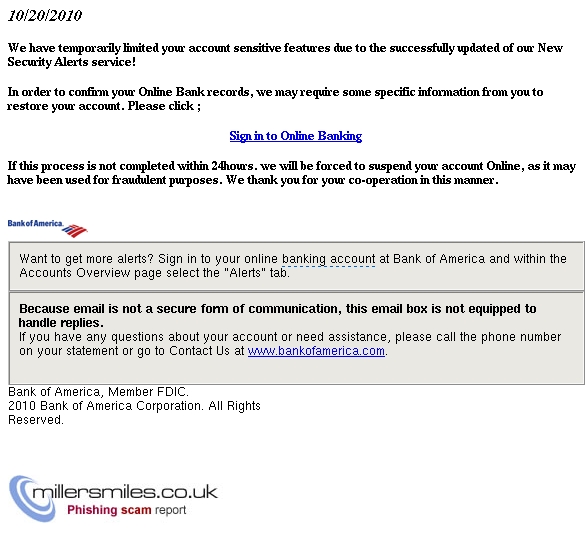
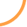
10/20/2010
WE HAVE TEMPORARILY LIMITED YOUR ACCOUNT
SENSITIVE FEATURES DUE TO THE SUCCESSFULLY
UPDATED OF OUR NEW SECURITY ALERTS
SERVICE!
IN ORDER TO CONFIRM YOUR ONLINE BANK
RECORDS, WE MAY REQUIRE SOME SPECIFIC
INFORMATION FROM YOU TO RESTORE YOUR
ACCOUNT. PLEASE CLICK ;
SIGN IN TO ONLINE BANKING
If this process is not completed within
24hours. we will be forced to suspend your
account Online, as it may have been
used for fraudulent purposes...
|
|
Click for full size image |
| |
| Website: |
|
|
| |
|
| Website was not online when we checked. It returned the error 404 |
|
|
 |
 |
 |
|
| |
 See our most recent scam reports See our most recent scam reports |
 |
Browse our scam report archives |
 |
Search |
Please send us any scam/phishing emails you have received by reporting them here
For access to our huge blacklist of domain names and to sign up to our live feed of ALL the scams we receive please take a look at our Honeytrap service
If you have received the email below, please remember that it is very common for these email scams to be redistributed at a later date with only slightly different content, such as a different subject or return address, or with the fake webpage(s) hosted on a different webserver.
We aim to report every variant of the scams we receive, so even if it appears that a scam you receive has already been reported, please submit it to us anyway.
|
| |
|
|
|
|